Docker networking refers to the networking capabilities and features provided by Docker to enable communication between containe...
Docker networking refers to the networking capabilities and features provided by Docker to enable communication between containers, between containers and the host system, and even between containers across different hosts in a networked environment. Docker uses a flexible networking model that allows containers to be connected to different types of networks, each serving a specific purpose.
Docker Network Types:
bridge
host
overlay
IPvLAN
Macvlan
None
Default Bridge Network:
When Docker is installed, a default bridge network named bridge is created. Containers attached to this network can communicate with each other by default, but they are isolated from the host machine and from containers on other bridge networks
User-Defined Bridge Networks:
Users can create their own bridge networks using the docker network create command. Containers connected to user-defined bridge networks can communicate with each other and with containers on the default bridge network.
Host Network:
Containers can be run with the --network host option, which makes them share the network namespace with the host. This means they share the same network interfaces and can directly bind to host ports.
Overlay Network:
Docker supports multi-host networking using overlay networks. Containers on different hosts can communicate with each other using overlay networks. This is especially useful in distributed or swarm-mode environments.
IPvLAN:
IPvLAN is an advanced driver that offers precise control over the IPv4 and IPv6 addresses assigned to your containers, as well as layer 2 and 3 VLAN tagging and routing.
This driver is useful when you’re integrating containerized services with an existing physical network. IPvLAN networks are assigned their own interfaces, which offers performance benefits over bridge-based networking.
Macvlan Network:
Docker supports the creation of Macvlan networks, allowing containers to be directly connected to a physical network. This enables containers to have their own MAC address and appear as physical devices on the network.
None:
IP addresses won’t be assigned to containers. These containments are not accessible to us from the outside or from any other container.

To List the networks in docker we need to use below command
Command: docker network ls

To check the Network details run the docker image as a container and use docker inspect to check the network of the particular docker container.
Command: docker inspect container-id
Example: docker inspect 0feb7bf95284

To Create the Custom Network
Command: docker network create --driver <driver-name> <bridge-name>
Example: docker network create --driver bridge test-network
Inspect the Newly created network
Command: docker network inspect bridge-name or network id
Example: docker network inspect 8d345e4c704d (or) test-network
If you want to create the network with your custom Range with a customer gateway you can use other options
To check the options use the below command
Command: docker network create –help
command: docker network create -d bridge --subnet network range with cidr --gateway gateway-ip Network-name
Example: docker network create -d bridge --subnet 192.168.0.0/16 --gateway 192.168.0.1 techiev
If we want to use our custom docker network for our container we can pass the --network option in the docker run command
Command: docker run -d --network=network_name dockerimage_name
Example: docker run -d --network=techiev httpd
Now we need to inspect and check the network ip of the httpd container.
Now we have the IP address within the given network range 192.168.0.0/16
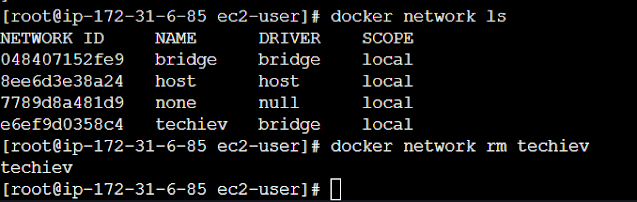
To remove all the unused Docker Networks
Command: docker network prune
Command: docker network rm Network name (or) id
Example: docker network rm techiev